Sometimes you may find yourself receiving emails from numerous sources demanding ransom in order to prevent sensitive information/images/videos being leaked to the public.
This would be a cause for concern for most people, especially if the senders of the emails claim to have access to your password and can paste it in plain text of the subject line to get your attention.
Here at Pipe Ten, we take our customer’s concerns very seriously, so we have written this guide to help answer some questions you may have.
Why am I receiving these emails?
Emails like this are often sent in hopes of tricking the receiver into handing over personal details or digital currency for monetary gain. In a most recent example of this, emails were sent requesting forms of cryptocurrency, such as Bitcoin(BTC) or Monero(XMR). This digital currency has actual real world value, which means they’re essentially demanding money from you. In the common examples we have seen recently, the options were pay the ransom of X amount of this cryptocurrency, or have private indecent videos leaked to your contacts list.
How have they gotten my password?
Some of these emails appear to be very threatening, with some even claiming to have access to one of your passwords. Whilst technology advances, so do the ways in which to exploit it. As data protection and information security changes rapidly and becomes more important each day, some companies are struggling to keep up. A lot of large companies, such as LinkedIn or Adobe, have had their customer’s accounts compromised, leading to a massive amount of username, passwords and personal emails being leaked to the public. This is clearly a big issue. Your details, once accessed, are then sold to the highest bidder on the dark web, where they’re then used for potential cyber crime, including for the emails demanding ransom that you may have been receiving.
Despite these large scale compromises, hackers have access to numerous ways of getting unauthorised access to account passwords, so it is important to think about security as often as you can.
What can I do about it?
First things first, don’t panic and don’t believe anything said in these emails. If they provide a password that is currently in use, change this immediately.
Firefox Monitor Service
Firefox provide a free to use monitoring system which allows you to check whether your email has been compromised. They’ll send you a report regarding this via the email you have given and will inform you of any compromises to the account’s password. They will also continue to monitor the email you have given and will notify you of any future data breaches your account occurs in.
Checking Email Headers
A good thing to do would be to find the email headers to get more information regarding where the email may have came from and whether it is a cause for concern or not. Analysing these often reveal much more than the email itself can.
Adding an SPF Record
Some emails of this nature manage to spoof your email address and make it look like the email has been sent from your account. We recommend adding an SPF record if you don’t have one in place already. This should help prevent people from being able to use your email address maliciously.
Anti Virus
Putting some form of local antivirus software on your devices will be incredibly useful. A common way for hackers to gain access to your passwords is by tricking you into installing malicious software onto your computer. They can easily log every keystroke you make if they wish once this has been installed. An antivirus solution will help scan your computer for any signs of infected files, quarantining and removing the issue if they find anything they see as a potential risk or threat. Some solutions also notify you if you’re in the process of downloading a malicious file, which is extremely useful in order to prevent it infecting your system.
Wi-Fi Public Networks
With free to the public Wi-Fi services being offered by more and more companies, this means there are more and more ways a hacker can gain access to information on your device. A lot of the Wi-Fi networks put in place in restaurants, hotels and airports are completely accessible to anyone, meaning anyone can connect without issue. If an attacker connects to the network, they can most likely capture network traffic and see everything you do, including what passwords you’re typing in and where if they look hard enough. The best way to counter this is to try and avoid connecting to public Wi-Fi when possible. If you need to access this Wi-Fi, it is recommended you use a VPN service on your device to help encrypt network traffic so that it’s unreadable if intercepted.
Using Secure Passwords
Creating a secure password is a high priority when using any software/device that requires them. As soon as someone has access to these passwords, they also have automatic access to whatever you use them for. It’s particularly frustrating if a mailbox becomes compromised as an attacker can see every email you have in your inbox, send emails supposedly from you, as well as reset passwords and lock you out of accounts, such as PayPal and so on. This is why it’s a must to have a strong, secure password.
Consequences of having a weak password include the possibility of it being brute forced or just having your password plain out guessed. Hackers won’t even need to gain access to your password illegitimately if they manage to just guess it. Don’t make things easier for them!
Use Biometrics/Facial Recognition on your Devices
Over the years, the technology industry has seen the introduction of biometrics and facial recognition on devices such as mobile phones and laptops. Before these were available, users had to rely on passcodes or simple patterns to keep their devices secure, which simply weren’t secure enough. These passcodes/patterns were often easy to guess, which lead to a lot of people being able to gain unauthorised access to a device. Now that mobile phones contain so much of our personal information, such as payment details and emails, we need to keep these much more secure. Although not completely foolproof, having biometrics/facial recognition on a device is much more secure than using a passcode/pattern.
Don’t Click Random Links
Sometimes you may receive emails telling you that you need to follow up with a verification process or that you need to pay an invoice that is unpaid. You will need to make sure in these emails that they are legitimate and if you’re unsure, to get in touch with the real company who the sender of the email may be trying to imitate. Sometimes senders of these emails will add links or attach files that it is highly recommended you don’t click on. A lot of these links will send you to a fake site where they will take a copy of your user credentials upon inputting them, or will send you to a download link , which will download and install a virus on your machine.
Example of a Ransom Email
I’m going to split an example of a ransom email into parts and analyse them to explain to you what each part means so you fully understand what is going on and why you shouldn’t worry.
Below you can see the subject and sender of the email highlighted in red. Cyber criminals have put the password into the subject line to try and grab your attention and scare you into actually reading the email.
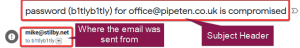
The sender in this particular case is a random email address that may have previously been compromised or is being spoofed. It is then being used by the criminals as a way to send spam emails whilst remaining undetected.
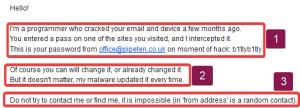
1: This is probably referring to a site that has been recently compromised. It is highly unlikely they have actually gained access to your emails or devices at all. For us, in this case, this was reinforced further by the fact the password they provided was very old and unused now, meaning it was even less likely they’d managed to gain unauthorised access. If the password is the same as one you use currently for an account, it is recommended you change this as soon as possible.
2: If the password given is the same password you have been using recently, it is recommended you change this, regardless of what is said here. It is also doubtful they have installed malware on your PC, but you can check this yourself using Antivirus software to scan your computer.
3: This part is true. There is no point replying to this email address as it will get you nowhere. You’re best off just ignoring this.
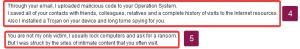
4: Again, it is highly unlikely they have gained access to your email, especially if it’s an old password. It’s even less likely they’ve uploaded malicious code to your operating system. It’s all just talk to try and cause panic and get the victim to pay ransom. They most likely won’t have access to any of your contacts, especially friends and relatives, as they have no way of telling the two apart from other contacts. A trojan being on your device due to the criminal is also unlikely. Just to be safe, you can always use an Antivirus software to give your device a scan. A trojan is just a term used to describe a piece of malicious software disguised to look like a legitimate piece of software. This is done in hopes it deceives the user and the software is hidden from plain sight.
5: A lot of the time, these emails are sent en-mass to a very large amount of targets. The scope is often in the hundreds of thousands, as this means there is a higher chance of catching more people out. The fact they say they usually lock computers and ask for a ransom is believable, but why haven’t they done it in this scenario? It’s most likely because they don’t actually have access to your device despite what they mentioned previously, so it just reinforces the idea they’re all talk with nothing to show for it. They will not know about any intimate sites you visit, they are just trying to use common scare tactics.
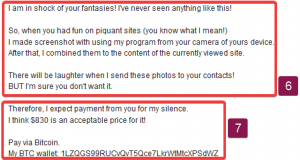
6: It has already been concluded by this point that it is very unlikely they have access to your device. I have also mentioned ways you may be able to check this using Antivirus software. They’re again just trying to use scare tactics. When they say they have sensitive content that they can share with everyone, it makes anyone uncomfortable at the thought of it being actually shared. They say this in hopes you meet their demands to prevent them doing this, when in reality, they probably have nothing on you to use against you.
7: This is where the attempt at ransom takes place. It is extremely common in ransom emails to say ‘Pay me X amount and I’ll not do what I’m threatening you with’. In reality, they’re not going to do anything if you don’t pay them, regardless of what they say. By this point we’ve already found numerous discrepancies in their email that disprove a lot of what they claim. Furthermore, what proof would you have that they’d not share this upon receiving the ransom anyway? They cannot be trusted.
Bitcoin is a form of cryptocurrency (digital money) that is very valuable at the time of writing this post. You can exchange real world currency for Bitcoin and use it in digital transactions as if it was real money. BTC(₿) is an abbreviation of it, the same way GBP is for the £. A BTC Wallet is just somewhere to store Bitcoin. These usually come with a unique address to send currency to , which has been provided here.
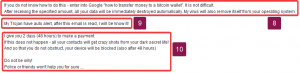
8: If they did have the data, there is no guarantee they will delete this. You can’t trust any attempts at ransom or the people behind them. We should have also concluded by this point there is barely any probability that there is a virus on the system and to confirm this further, an antivirus software will help check this for you.
9: See points 4 and 8. By this point you should have confirmation there isn’t a Trojan on your system. It will also be highly unlikely they’ll be tracking every single email of the thousands of emails they’ve sent and sifting through them to see who has read them or not. It is just a scare tactic to try and stop you wanting to ignore their demands. Read responses are only sent if you specifically tell, or set, your email client to send them.
10: By this point you should be able to tell they’re bluffing. They haven’t had access to your contacts (see 4) and shouldn’t be able to block your device as they don’t have access to it (see 5). You should be able to ignore this email without worrying about them going through with their threats as the majority of it is just untrue and is just trying to scare you into paying the ransom.

Classification: Public
Last saved: 2019/11/27 at 16:03 by Jamie
