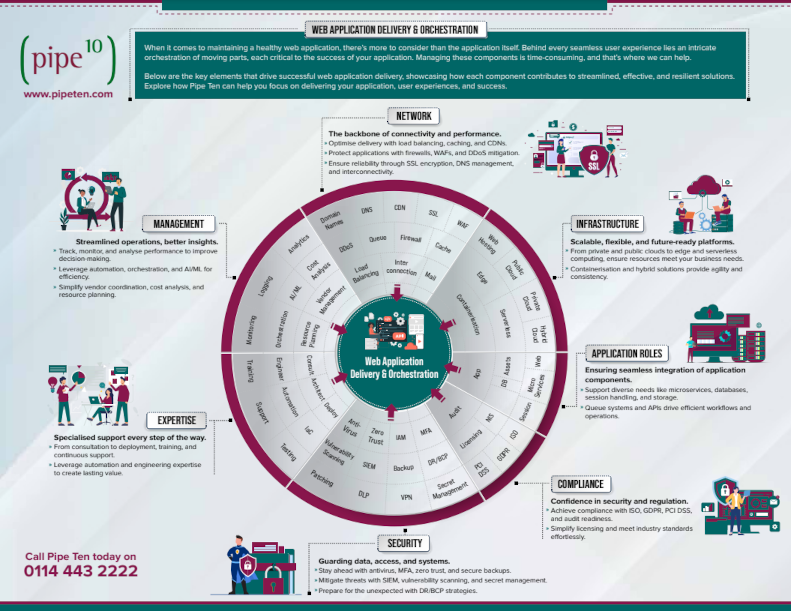
This is the sixth in our series of insights which seek to explore and simplify the topic of SSL (and TLS) in the context of web application hosting. In our previous insight, we looked at TLS and Versions; in this insight, we’ll explore what web server headers you should consider when configuring your web service.
What is a web server header?
Imagine you’re sending a letter to a friend. Along with the letter, you also include a note that tells your friend some extra information, like how to handle the letter, if it’s urgent, or if they should keep it secret. In the world of the internet, when a web server sends data to your computer, it does something similar using something called “web server headers.” Web server headers are like special notes with the data you get from a website. These notes don’t appear on the webpage you see, but they tell your web browser (like Chrome, Firefox, or Safari) some crucial instructions about handling the website’s data. 
Headers to prioritise
Strict-Transport-Security (HSTS)
This header is crucial for enforcing secure (HTTPS) connections to the server. The Strict-Transport-Security header tells the browser to connect to the server only using a secure connection for a set period. This helps prevent downgrade attacks and cookie hijacking.
Content-Security-Policy (CSP)
While not specific to SSL, this header is essential for security. It helps prevent cross-site scripting (XSS) and data injection attacks. CSP can specify which domains the browser should consider valid sources for executable scripts.
Other headers
X-Content-Type-Options
This header prevents Internet Explorer and Google Chrome from MIME-sniffing a response away from the declared content type. This is a security feature that helps prevent attacks based on MIME-type mismatch.
X-Frame-Options
This header can be used to control whether a browser should be allowed to render a page in a <frame>, <iframe>, <embed>, or <object>. Sites can use this to avoid clickjacking attacks by ensuring their content is not embedded into other sites.
X-XSS-Protection
This header is used to configure the built-in reflective XSS protection found in some web browsers. Using Content-Security-Policy properly is a more modern and effective way to prevent XSS attacks, but this header can still be relevant in specific scenarios.
Referrer-Policy
This header governs which referrer information, sent in the Referrer header, should be included with requests. It’s a security feature that helps control the amount of information shared via HTTP headers.
Expect-CT
This header allows sites to opt into reporting and enforcement of Certificate Transparency requirements, which prevents the use of miss issued certificates for the site by ensuring that all certificates for the site are publicly logged.
Public-Key-Pins (HPKP)
This header associates a specific cryptographic public key with a particular web server to decrease the risk of MITM attacks with forged certificates. However, it should be noted that HPKP has been removed from most major browsers due to the risks associated with misconfiguration and the availability of better mechanisms like Certificate Transparency.
Keep updated with the latest from Pipe Ten by subscribing below.
More in the Simplifying SSL/TLS series
- SSL Basics – What is SSL?
- SSL Certificate Terminology
- EV vs DV vs OV vs FREE SSL Certificates
- Certificate Authorities and The Signing Process
- TLS and Versions
- Web Server Headers
- Mixed Content Warning
- Testing & Tools
Author: Carl Heaton
Carl is a founder of Pipe Ten and uses his role as Technical Director to drive the company’s vision to transform business online in delivering it’s mission to forge agile technical partnerships that accelerate web success. Carl boasts an illustrious career spanning over two decades, starting as a fledgling web developer in his teens, he swiftly ascended the ranks, honing his skills in architecting secure web application infrastructure. With his finger on the pulse of emerging web technologies, Carl has tracked and influenced the ever changing world of cyber security, internet governance, industry regulations and information security compliance ensuring Pipe Ten successfully achieved and maintain ISO/IEC 27001 certification.